Information Systems Security-A Trade-off Between Security and Freedom
- Example: Organizations can increase the security of their information systems by taking away users' freedom to choose their own passwords and force them to choose stronger passwords that are difficult for hackers to crack.
- Goal: Find an appropriate trade-off between the risk of loss and the cost of implementing safeguards.
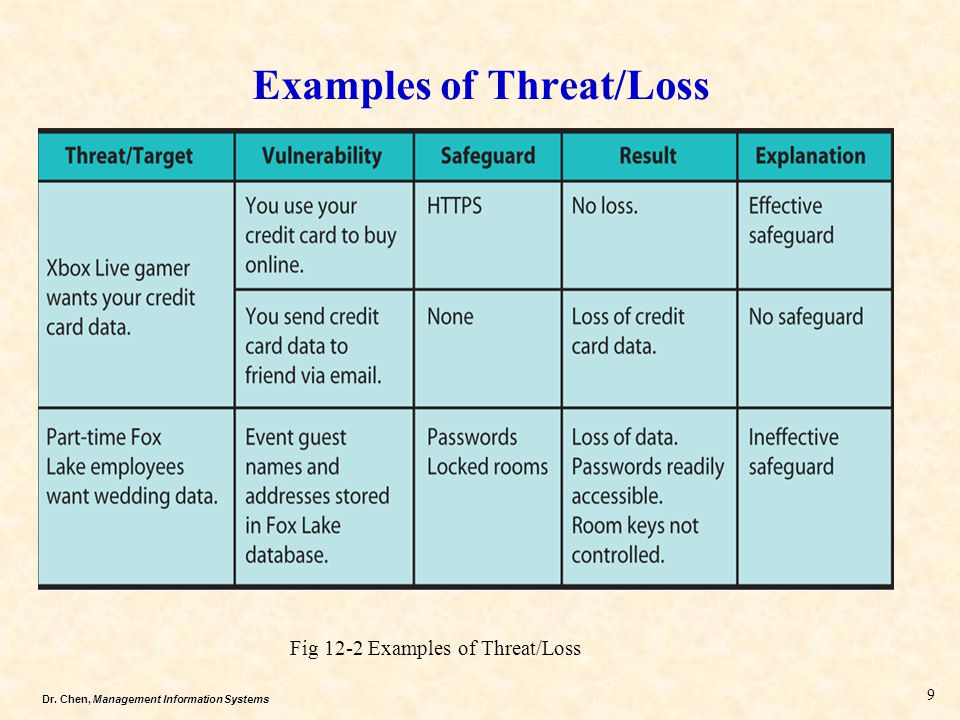
- Threat- is a person or organization that seeks to obtain or alter data or other IS assets illegally, without the owner's permission and often without the owner's knowledge.
- Vulnerability- is an opportunity for threats to gain access to individual or organizational assets.
- Example of Vulnerability: Making an online purchase using a credit card, the credit card data is transmitted over the Internet and it vulnerable to threats.
- Safeguard- is some measure that individuals or organizations take to block the threats from obtaining the asset.
- Target- is the asset that is desired by the threat.
- Sources: Human errors and mistakes, Computer crime, and Natural events and disasters.
What Types of Security Loss Exist?
- Unauthorized data disclosure
- Pretexting- occurs when someone deceives by pretending to be someone else.
- Phishing- is a similar technique for obtaining unauthorized data that uses pretexting via email.
- Phisher- pretends to be a legitimate company and sends an email requesting confidential data.
- Examples: Account numbers, Social Security numbers, Account passwords, etc.
- Spoofing- is another term for someone pretending to be someone else.
- IP spoofing- occurs when an intruder uses another site's IP address to masquerade as that other site.
- Email spoofing- is a synonym for phishing.
- Sniffing- is a technique for intercepting computer communications.
- Wired networks: Sniffing requires a physical connection to the network.
- Wireless networks: No such connection is required.
- Wardrivers- simply take computers with wireless connections through an area and search for unprotected wireless networks.
- Hacking-breaking into computers, servers, or networks to steal data such as customer lists, product inventory data, employee data, and other proprietary and confidential data.
- Natural disasters
- Incorrect data modification
- Examples: Incorrectly increasing a customer's discount, Incorrectly modifying an employee's salary, earned days of vacation, or annual bonus.
- Can occur through human error when employees follow procedures incorrectly or when procedures have been designed incorrectly.
- System Error- "lost-update problem"
- Hacking
- Natural Disasters
- Faulty service
- Can include incorrect data modification
- Can include systems that work incorrectly by sending the wrong goods to a customer or the ordered goods to the wrong customer, inaccurately billing customers, or sending the wrong information to employees.
- Human can make procedural mistakes.
- System developers can write programs incorrectly or make errors during the installation of hardware, software programs, and data.
- Usurpation- occurs when computer criminals invade a computer system and replace legitimate programs with their own, unauthorized ones that shut down legitimate applications and substitute their own processing to spy, steal and manipulate data, or archive other purposes.
- When service is improperly restored during recovery from natural disasters.
- Denial of service (DoS)
- Example: Humans can inadvertently shut down a Web server or corporate gateway router by starting a computationally intensive application.
 |
| Example of DoS |
- Loss of infrastructure
- Theft and Terrorist events
- Natural Disasters present the largest risk, these can destroy data centers and all that contain them.
- Examples: Fire, Flood, Earthquake
- Advanced Persistent Threat (APT)- is a sophisticated, possibly long-running computer hack that is perpetrated by large, well-funded organizations such as governments.
- Can be a means to engage in cyberwarfare and cyberespionage.
How Big Is the Computer Security Problem?

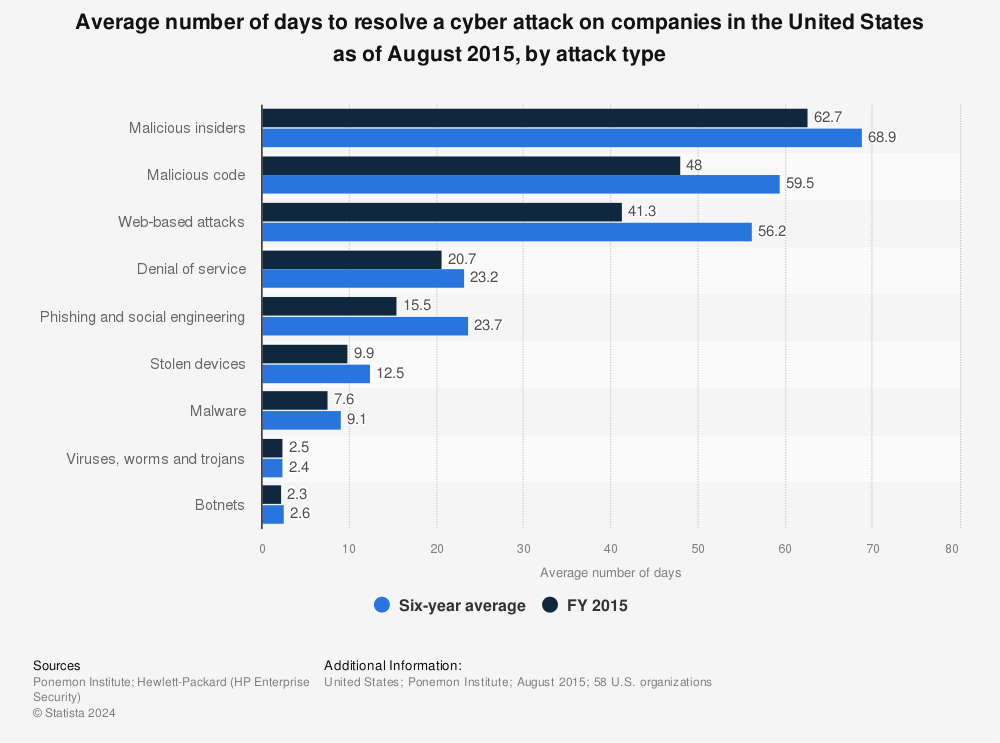
- No One Really Knows because...
- There are no standards for tallying crime costs.
- All the studies on the cost of computer crime are based on surveys.
- The most that can be done is to look for trends and compare year-to-year data, assuming the same methodology is used by the various types of survey respondents.


According to the textbook, Using MIS, the 2014 Cost of Computer Crime Study resulted in the following:
- Malicious insiders are an increasingly serious security threat.
- Business disruption and data loss are principal costs of computer crime.
- Survey respondents believe negligent employees, personal devices connecting to the corporate network, and the use of commercial cloud-based applications pose a significant security threat.
- Security safeguards work. (pg 394)
How Should You Respond to Security Threats?
- Intrusion Detection Systems (IDS)- is a computer program that senses when another computer is attempting to scan or access a computer or network.
- If these come from outside the country, there is nothing you can do about them except use reasonable safeguards.
- Brute force attack- in which the password cracker tries every possible combination of characters.
- Use long passwords with no words, 10 or more characters, and a mix of letters, numbers, and special characters.
- Use different passwords for different sites.
- Never send passwords, credit card data, or any other valuable data in email or IM.
- Cookies- are small files that your browser receives when you visit Web sites.
- The best safeguard is to remove your browsing history, temporary files, and cookies form your computer and to set your browser to disable history and cookies.
- CCleaner- a free, open source product that will do a thorough job of securely removing all such data.
- Make a backup of your computer before using CCleaner.

How Should Organizations Respond to Security Threats?
Senior management needs to address two critical security functions: Security Policy and Risk Management.

Senior management needs to address two critical security functions: Security Policy and Risk Management.
- At a minimum, the policy should stipulate:
- What sensitive data the organization will store.
- How it will process that data.
- Whether data will be shared with other organizations.
- How employees and others can obtain copies of data stored about them.
- How employees and others can request changes to inaccurate data.
- Risk Management
- Risk cannot be eliminated
- Manage risk means to proactively balance the trade-off between risk and cost.
- This trade-off varies from industry to industry and from organization to organization.
- Example: Financial institutions (Higher investment) vs. Bowling alley (Lower investment).

How Can Technical Safeguards Protect Against Security Threats?
- Technical safeguards
- Involve the hardware and software components of an information system.
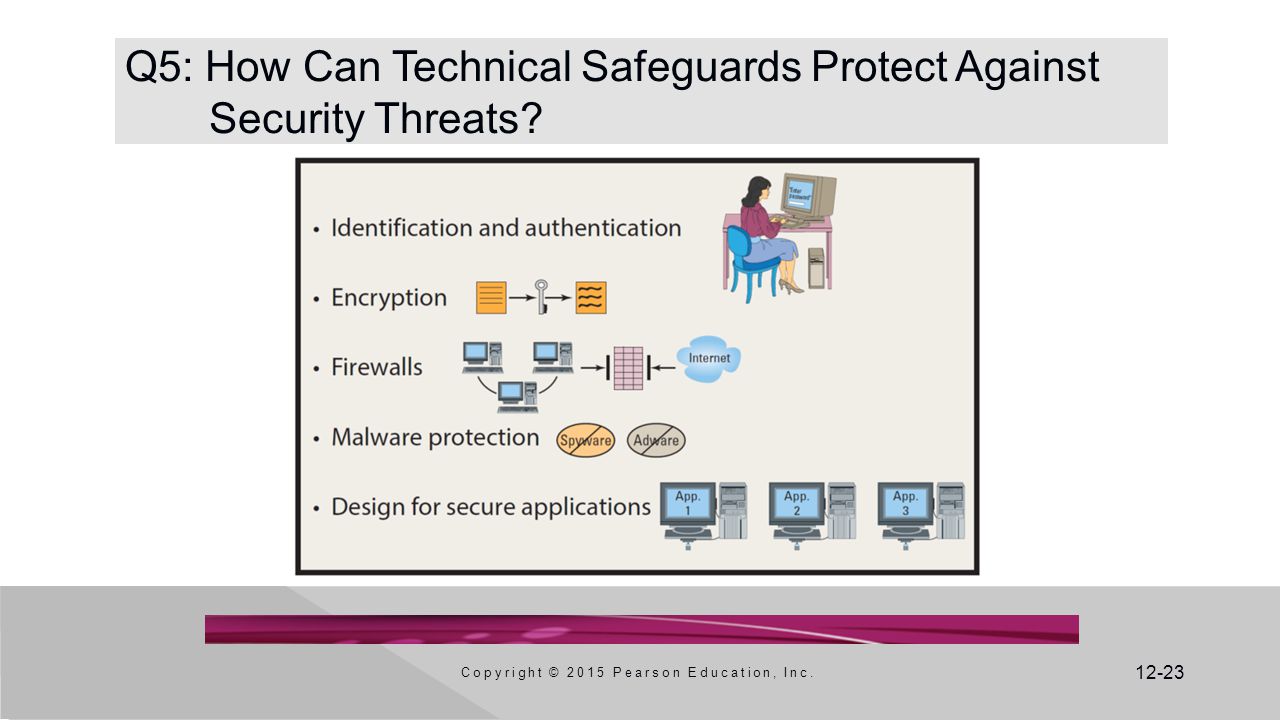
- Identification- "User"name identifies the user
- Authentication- "password" authenticates that user.
- Smart card- a plastic card similar to a credit card.
- Instead of a magnetic strip, the smart card has a microchip which holds far more data.
- Users of smart cards are required to enter a personal identification number (PIN) to be authenticated.
- Biometric authentication- uses personal physical characteristics.
- Examples: Fingerprints, facial features, and retinal scans to authenticate users.
- Provides strong authentication, but the required equipment is expensive.
- It is also in the early stages of adoption.
- Encryption- is the process of transforming clear text into coded, unintelligible text for secure storage or communication.
- Considerable research has gone into developing encryption algorithms (procedures for encrypting data) that are difficult to break.
- Common methods: DES, 3DES, and AES
- Key- is a string of bits used to encrypt the data. It "unlocks" a message, but it is a string of bits, expressed as numbers or letters, used with an encryption algorithm.
- Decrypting (decoding)- the key is applied to the coded message to recover the original text.
- Symmetric encryption- the same key is used to encode and decode.
- Asymmetric encryption- two keys are used, one encodes the message and the other key decodes the message.
- Symmetric encryption is much simpler and faster than asymmetric.
- Public key encryption- a special asymmetric encryption.
- used on the Internet, each site is a "public key" for encoding messages and a "private key" for decoding them.
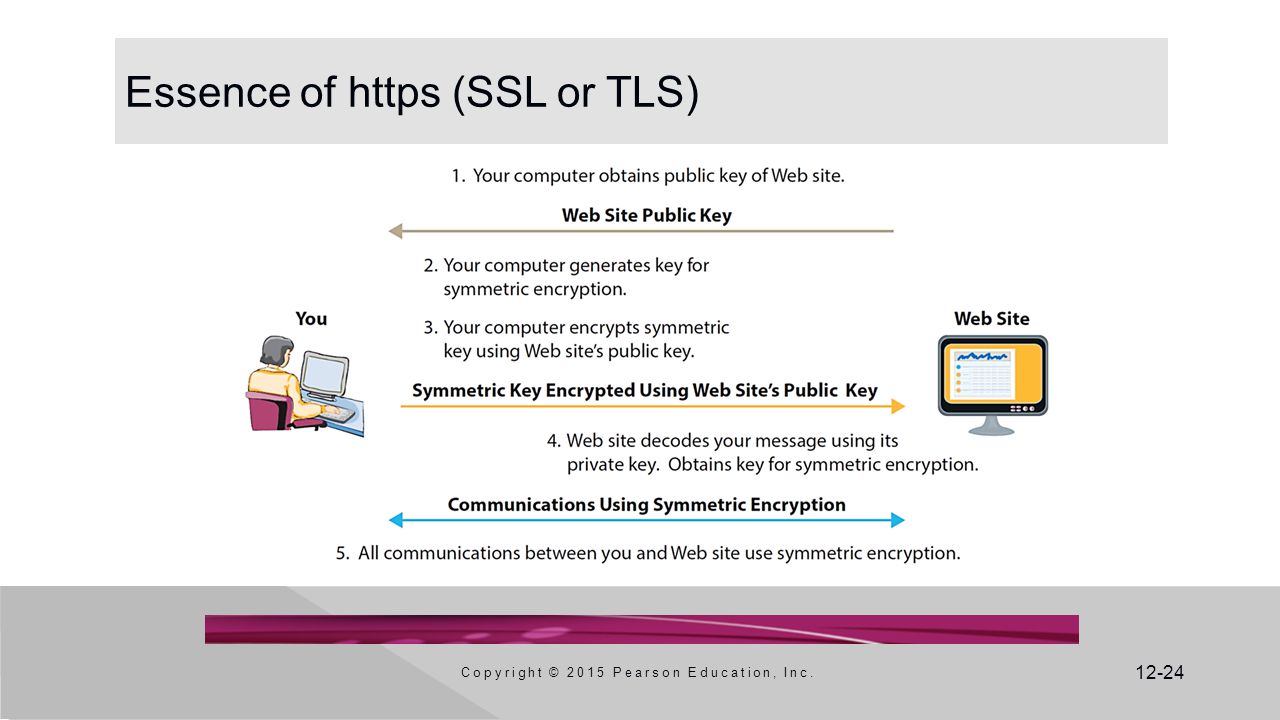
- https- most secure communication over the Internet uses this protocol.
- With https, data are encrypted using a protocol Secure Sockets Layer (SSL), also known as Transport Layer Security (TLS).
- Both use a combination of public key encryption and symmetric encryption.
- Firewall- is a computing device that prevents unauthorized network access, simply a filter.
- Can be a special-purpose computer.
- Can be a program on a general-purpose computer or on a router.
- Perimeter firewall- sits outside the organizational network; it is the first device that Internet traffic encounters.
- Internal firewalls- inside the organizational network.
- Packet-filtering firewall- examines each part of a message and determines whether to let that part pass. To make this decision, it examines the source address, the destination address(es), and other data.
- Can prohibit outsiders from starting a session with any user behind the firewall.
- Can disallow traffic from particular sites, such as known hacker addresses.
- Packet-filtering firewalls are the simplest type of firewall.
- No computer should connect to the Internet without firewall protection.

Spyware and Adware Symptoms
- Slow system startup
- Sluggish system performance
- Many pop-up advertisements
- Suspicious browser homepage changes
- Suspicious changes to the taskbar and other system interfaces
- Unusual hard-disk activity
Malware definitions- patterns that exist in malware code should be downloaded frequently.
SQL injection attack- occurs when users enter a SQL statement into a form in which they are supposed to enter a name or other data.
- If the program is improperly designed, it will accept this code and make it part of the database command that it issues.
- Improper data disclosure and data damage and loss are possible consequences.
- A well-designed application will make such injections ineffective.
How Can Data Safeguards Protect Against Security Threats?
- Data safeguards- protect databases and other organizational data.
- Two organizational units are responsible for data safeguards.
- Data administration- refers to an organization-wide function that is in charge of developing data policies and enforcing data standards.
- Database administration- refers to a function that pertains to a particular database.
- Example: ERP, CRM, and MRP
- Key escrow- a safety procedure, when data are encrypted and a trusted party should have a copy of the encryption key.

How Can Human Safeguards Protect Against Security Threats?
Human safeguards- involve the people and procedure components of information systems.
- In general, these result when authorized users follow appropriate procedures for system use and recovery.

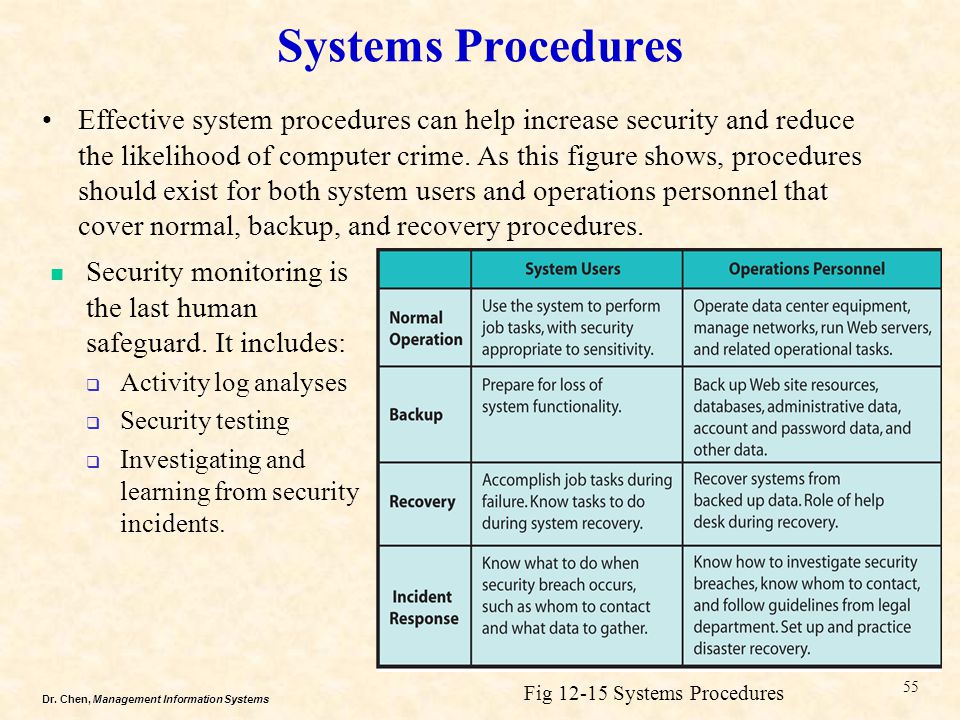
How Should Organizations Respond to Security Incidents?

2026?

As of June 2015, privacy advocates were outraged at the existence of PRISM, the intelligence program by which the National Security Agency (NSA) requested and received data about Internet activities from major Internet providers.
- They claimed their privacy, or freedom from being observed by other people, was being destroyed in the name of security, or state of being free from danger.
"We can hope the revelation of existence of PRISM will spark a public conversation on the balance of national security and data privacy" (Using MIS, pg 414).

CAUTION! We will still be exposed to computer crimes!

No comments:
Post a Comment