
Future of Cloud Computing
Cloud- the elastic leasing of pooled computer resources over the Internet. A cloud symbolizes the Internet, as shown in the above picture. Elastic- the computing resources leased can be increased or decreased dynamically, programmatically, in a short span of time and that organizations pay for just the resources they use. Pooled- many different organizations use the same physical hardware; they share that hardware through virtualization. Over the Internet- the computer industry settled on a set of standard ways of requesting and receiving services over the Internet.
Pro's to Cloud Computing
- Small capital requirements
- Speedy development
- Superior flexibility and adaptability to growing or fluctuating demand
- Known cost structure
- Possibly best-of-breed security/disaster preparedness
- No obsolescence
- Industry-wide economies of scale, hence cheaper
Con's to Cloud Computing
- Dependency of Vendor
- Loss of control over data location
- Little visibility into true security and disaster preparedness capabilities
Why Cloud Computing Now?
- Processors, data communication, and data storage are so cheap that they are nearly free.
- Virtualization technology enables the near instantaneous creation of a new virtual machine.
- Internet-based standards enable cloud-hosting vendors to provide processing capabilities in flexible yet standardized ways.
While cloud computing sounds great and we can see that there are more benefits than negatives to using the cloud, there are some organizations where cloud computing may not make sense. These are organizations that by law or industry, they have a standard practice to have physical control over their data. In the future, the IRS, Financial institutions like banks for example might be pressured to create and maintain their own infrastructure to keep up with advanced technology and still follow protocol.
What Network Technology Supports the Cloud?

Four types of Basic Networks
Network- a collection of computers that communicate with one another over transmission lines or wirelessly. Protocol- a set of rules and data structures for organizing communications.
- Personal area network (PAN)- devices connected around a single person, most PAN devices connect wirelessly to other devices located within 10 meters.
- Local area network (LAN)- computers connected at a single physical site, the number of connected computers can range from two to several hundred in a single geographic location on the premises of the company that operates the LAN. An organization can place communications lines wherever it wants because all lines reside on its premises.
- Wide area network (WAN)- computers connected between two or more separated sites, different geographic locations. The computers for a single campus can be connected via a LAN. The computers for a campus located on multiple locations must be connected via a WAN. An organization that needs to connect computers in two different states, must contract with a communications vendor licensed by the government and that already
- The Internet and internets- Networks of networks. An internet- a network of networks. Internets connect LANs, WANs, and other internets. Additionally, "the Internet" is the collection of networks you use when you send an email or access a Web site. Finally, an intranet- private networks of networks. Soemtimes it is a private internet used exclusively within an organization.
Components of a LAN
- Small office or home office (SOHO)- a typical place where LAN is used, devices can be wired or wireless connections.
- Institute for Electrical and Electronics Engineers (IEEE)- sponsors committees that create and publish protocol and other standards.
- IEEE 802 Commmittee- committee that addresses LAN standards, LAN protocols always start with 802.
- IEEE 802.3 protocol- is used for wired LAN connections.
- Ethernet, specifies hardware characteristics, such as which wire carries which signals. Also described how messages are to be packaged and processed for wired transmission over the LAN.
- 10/100/1000 Ethernet- most PCs today support products conformed to the 802.3 specification and allow for transmission at a rate of 10, 100, or 1000 Mbps (megabits per second). Bits- express communication speeds
- IEEE 802.11 protocol- several versions exist
- IEEE 802.11ac-the most current version as of 2015, it allows speeds of up to 1.3 Gbps.
- Bluetooth- another common wireless protocol used to make PAN conncections.
- Examples: Wireless mice, keyboards, printers, headphones, smartwatches and fitness trackers.
Important Functions for Connecting to the Internet- An Internet service provider (ISP)
- It provides you with a legitimate Internet address.
- It serves as your gateway to the Internet.
- ISP receives communication from your computer and passes them on to the Internet, and it receives communications from the Internet and passes them on to you.
- ISPs pay for the Internet.
- They collect money from their customers and pay access fees and other charges on your behalf.
Three Common Alternatives for Connecting to the Internet
- Digital subscriber line (DSL)- operates on the same line as voice telephones, it does not interfere with voice telephone services.
- DSL data transmission and telephone conversations can occur simultaneously.
- Digital subscriber lines use their own protocols for data transmission.
- Cable lines- provide high-speed data transmission using cable television lines.
- The cable company installs a fast, high-capacity optical fiber cable to a distribution center in each neighborhood it serves.
- At the distribution center, the optical fiber cable connects to a regular cable-television cables that run to subscribers' homes or businesses.
- Cable signals do not interfere with TV signals, and they use their own protocols.
- WAN wireless- connecting a computer, mobile device, or other communicating device via a WAN Wireless connection.
- Examples: Amazon.com's Kindle uses Sprint wireless network to provide wireless data connections.
- The Iphone uses a LAN-based wireless network if one is available and a WAN wireless network if not.
- The LAN-based network is preferred because performance is considerably higher.
As stated above, connecting your LAN to the Internet has 3 important functions. As the functions are working, there are other processes taking place. It is important to understand the process of an Internet, then get to know how the Cloud works.
Know these Terms:
- Hop-is the movement from one network to another.
- Packet- the message that moves across the Internet.
- Carriers- networks owned by large telecommunications providers
- Examples: Sprint, ATT&T, Verizon Business, and XO Communications
- Peering- When large carriers exchange traffic without charging each peer access fees via agreements, but carriers do charge subscription fees from end users.
- Net neutrality- the principle where all data is treated equally.
- IP address- an Internet address with a number that identifies a particular device.
- IPv4- has a 4-decimal dotted notation
- IPv6- has a longer format
- Public IP addresses- identify a particular device on the public Internet. Not as safe as Private IP addresses.
- Internet Corporation for Assigned Names and Numbers (ICANN)- a public agency that oversees the assignment of Public IP addresses because they must be unique and worldwide.
- Private IP addresses- identify a particular device on a private device on a private network, usually on a LAN controlled by a LAN device. Safe from attackers because they cannot attack private IP addresses, they can only send packets to Public IP addresses.
- Domain name-is a worldwide-unique name that is affiliated with public IP address.
- When an organization/individual wants to register a domain name, it goes to a company that applies to an ICANN-approved agency to do so.
- Several (or many) domain names can point to the same IP address.
- The affiliation of domain names with IP addresses is dynamic. The owner of the domain name can change the affiliated IP addresses at its discretion.
- Uniform Resource Locator (URL)- is an address on the Internet, commonly consists of a protocol followed by a domain name or public IP address.,
Processing on a Web Server
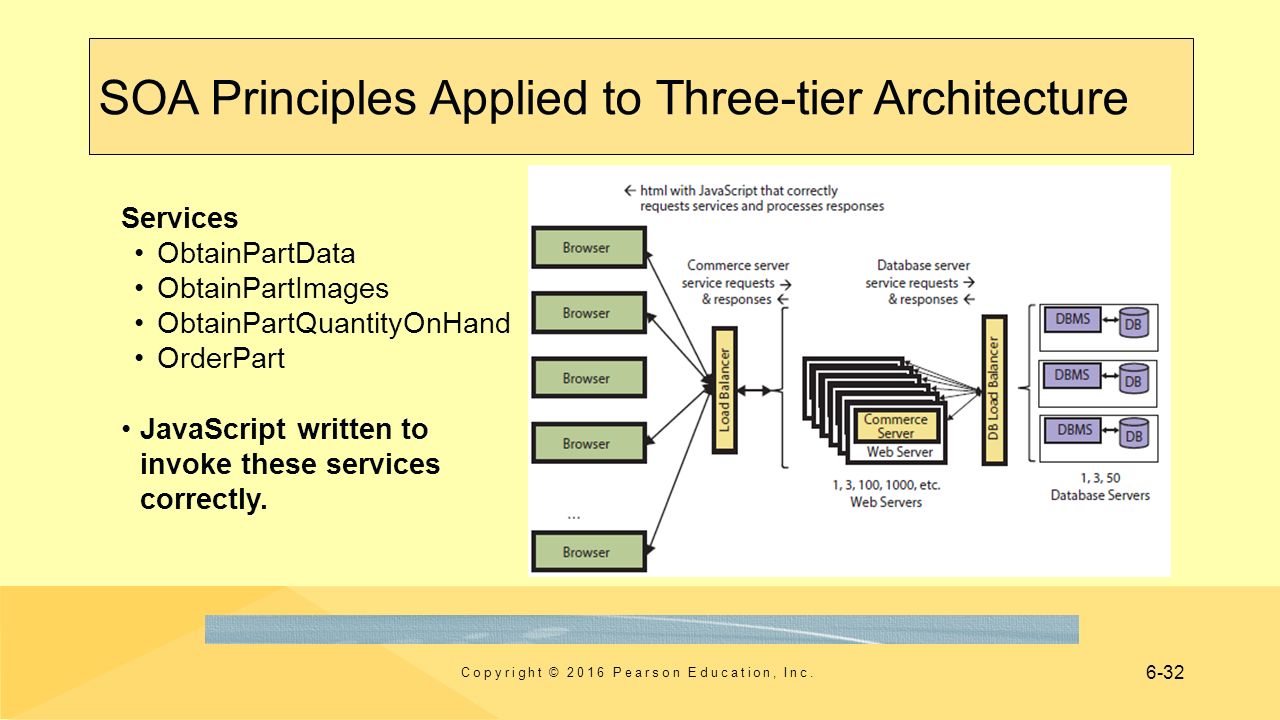
- Three-tier architecture- a design of user computers and servers that consists of 3 categories, or tiers.
- User tier-consists of computers, phones, and other mobile devices that have browsers that request and process Web pages.
- Server-tier- consists of computers that run on Web servers and process application programs.
- Database-tier- consists of computers that run a DBMS that processes requests to retrieve and store data.
- Web page- a document coded in, usually html and maybe includes CSS, JavaScript, and other data.
- Web servers- programs that run on a server-tier computer and manage traffic by sending and receiving Web pages to and from clients.
- Commerce server-is an application program that runs on a server-tier computer.
- Typical functions- obtain product data from a database, manage the items in a shopping cart, and coordinate the checkout process.
Service-Orientated Architecture (SOA)
- Service-oriented architecture (SOA)- all interactions among computing devices are defined as services in a formal, standardized way.
- TCP/IP Protocol Architecture- the basic plumbing of the Internet governed by protocols that are defined according to these arrangements. The architecture is made up of 5 layers.
- Hypertext Transfer Protocol (http)- is the protocol used between browsers and Web servers
- https-are secured versions of http, indicating you can safely send sensitive information like credit card numbers.
- Simple Mail Transfer Protocol (smtp)- is used for email transmission (along with other protocols)
- File Transfer Protocol (ftp)- is used to move files over the Internet.
- Google Drive and Microsoft OneDrive use ftp behind the scenes to transmit files to and from their cloud servers to your computer.
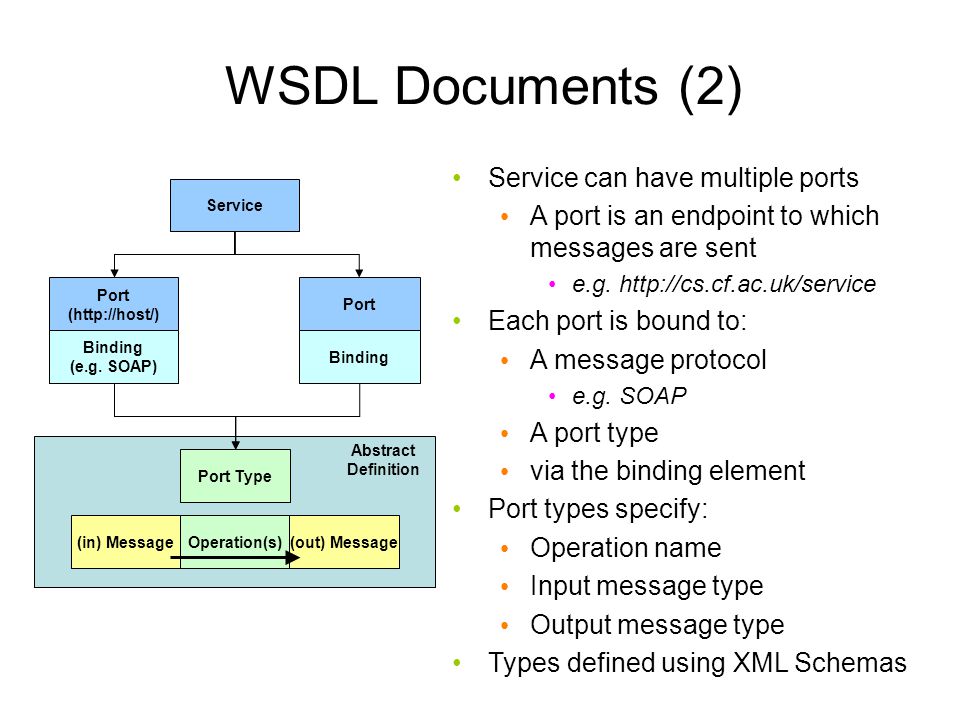
4 Standards Used Extensively for Web Services and the Cloud
 |
 |
How Do Organizations Use the Cloud?
- Software as a service (SaaS)- provides not only hardware infrastructure, but an operating system and application programs as well.
- Office 365, Exchange, Skype for Business, and SharePoint applications are provided as a service "in the cloud"
- Platform as a service (PaaS)- vendors provide hosted computers, an operating system, and possibly a DBMS.
- Amazon EC2 provides servers with Windows Server or Linux installed.
- Infrastructure as a service (IaaS)- the cloud hosting of a bare server computer or data storage.
- Amazon.com licenses S3 (Simple Storage Service), which provides unlimited, reliable data storage in the cloud.
- Content delivery network (CDN)- is a system of hardware and software that stores user data in many different geographical locations and makes those data available on demand.
- Benefits
- Decreased, even guaranteed, loadtime
- Reduced load on origin server
- Increased reliability
- Protection from DOS attacks
- Reduced delivery costs for mobile users
- Pay-as-you-go

How Falcon Security Use the Cloud?
- Saas products
- Faclon can use the following Gooogle Mail, Google Drive, Office 365, Salesforce.com, Microsoft CRM OnLine or others.
- Paas products
- Falcon can purchase licenses to permit replication because Amazon.com will replicate it when it increases servers.
- As of May 2015, Amazon.com offers the following DBMS products with EC2: Amazon Relational Database Service (RDS), Amazon DynamoDB, MongoDB, Amazon ElastiCache, and Amazon Redshift.
How Can Organizations Use Cloud Services Securely?
- Virtual private network (VPN)- uses the Internet to create the appearance of private, secure conncections.
- Tunnel- a virtual, private pathway over a public or shared network from the VPN client to the VPN server.
- To secure VPN communications over the public Internet, the VPN client software encrypts, or codes, messages so their contents are protected from snooping. Later when the VPN server receives the message, it strips its address off the front of the message, decrypts the coded message, and sends the plain text message to the original address inside the LAN.
- Secure private messages are delivered over the public Internet.
- Private cloud- is a cloud owned and operated by an organization for its own benefit.
- To create a private cloud, the organization creates a private internet and designs applications using Web services standards.
- Private clouds provide security within the organizational infrastructure but do not provide secure access from outside that infrastructure.
- Private clouds provide the advantages of elasticity, but to questionable benefit.
- Virtual private cloud (VPC)- is a subset of a public cloud that has highly restricted, secure access.
- Using VPC an organization can store its most sensitive data on its own infrastructure and store the less sensitive data on the VPC.
2026?
Good News-the organizations can readily obtain elastic resources at very low cost, and the overall size of the cloud is getting bigger.
Bad News- According to Computerworld, Apple Web farm's building employs an operation staff of 50 people, which spread over three shifts, 24-7, means that not many more than eight people will be running that center at an one time.
New Job Opportunities
- Remote action systems- information systems (IS) that provide computer-based activity or action at a distance.
- Telediagnosis- is a remote action system that healthcare professionals use to diagnose illness for patients in rural or remote areas.
- Telesurgery- uses telecommunications to link surgeons to robotic equipment at distant locations.
- Telelaw enforcement- an example is from RedFlex system that uses cameras and motion-sensing equipment to issue tickets for a red light violation and speeding violation.










